First start your wifi NIC.
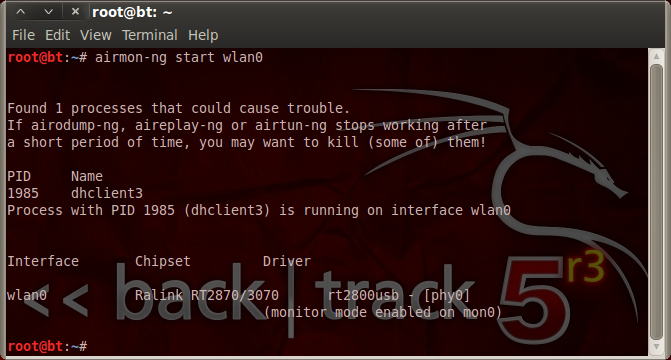
Then configure it for “monitoring / scanning” mode.

You’ll see similar to this screenshot. I let it scan for 10 minutes. Where you see “<length: 8>” is where a hidden wifi network SSID is, a little more time will reveal the SSID. I dropped the font size down so I could get the console window to fit the SSID’s so you could see the full names. After letting the scan run for awhile hit CTRL + C to drop back to command line then highlight the MAC of the network you want to crack and copy it. As far as I’m concerned anyone who sets their SSID as “yesitssecure” is asking to be proved otherwise.

Type in the “reaver” command and options and paste the MAC followed by -vv then enter. You’ll see it start by scanning the channels, once it locks onto the SSID it will start brute-force attack immediately. This typically takes 9-10 hours.

Here’s what you can expect to see shortly after initializing reaver. Progress in % & stats showing an estimate of seconds per pin.
Here you can see it completed in roughly 9 1/2 hours from the time I started the scan. Shows you a little more statistics info plus some real useful info such as the password to connect to the wifi (the whole reason we’re doing this to begin with right?). The password is the PSK value if you hadn’t figured that out. The WPS PIN is the number on the bottom of the wifi router used to connect to it easily for the first time which you’re suppose to enter a password that will be used from then on after.
According to the homework I’ve done these routers are easily cracked by this method and WPS should be disabled to avoid this security vulnerability, I’ve also read that disabling this feature doesn’t really disable it and makes it impossible to prevent cracking the device utilizing this method. I have DD-WRT on my wifi so hopefully those guys actually have it disabled rather than providing the false sense of security as the manufactures do by just showing a radio button that visually shows the feature is disabled when really it isn’t.

One last thing to note. From my experience the wifi router management browser interface is usually either still left as the original default login info set by the manufacture or all they changed was the password to the same one they set the wifi connection password to which we just cracked. If it’s neither there’s a tool in BackTrack that will crack the web interface but I have yet to need to. At some point I do want to try it out there and of course if I can successfully get it to work I’ll do a post about it. I hope you enjoyed this and found it educational.
There’s a “WEP Cracking with BackTrack 5 R3” post I did back in October last year if you are interested in how to crack wifi routers utilizing that authentication method. These can be cracked in half the time of the WPA2.
I’ve been meaning to do this post since I did the WEP post. I needed to whittle down the best way to do it because everything I found online as far as blogs and videos on youtube go, the methods didn’t actually work for whatever reason. I have found through trial and error on my own there were far many more steps involved and the process was much more complicated using other peoples methods to achieve the same results I have with at least half of the keystrokes & effort.
Source < http://unxvm.net >
Yahoo:minhtuyen909 Mail: tmtuyen89@gmail.com Blog: tranminhtuyen.wordpress.com






